I've just finished testing RSA SecurID Token authentication with FBA on ISA Server 2006, below are the steps that I followed.
We followed some notes at the
MS TMG Technet Blog for the actual ISA Rule base configuration which is pretty straightforward.
Register ISA Servers as Authentication Agents in RSA AM 7.1
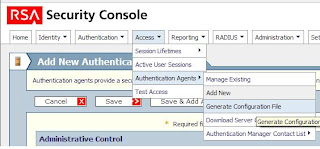
Open the RSA AM Security Console and go to 'Access', 'Authentication Agents' and 'Add New'.
Complete the details for the ISA Server as an 'Authentication Agent' including the FQDN and IP Address. I also set the 'Agent Type' to 'Web Agent' (Unlike in the screenshot).
Generate RSA AM Config File
In the Security Console go to 'Access', 'Authentication Agents' and 'Generate Configuration File'.
Check the setting and then click the 'Generate Config File' button to download the configuration file.
Click 'Download Now' to start the configuration file download.
Download and extract the sdconf.rec from the AM_Config.zip once downloaded
Copy sdconf.rec to C:\Windows\System32\ and C:\Program Files\Microsoft ISA Server\sdconfig\ on all relevant ISA Servers.
Set Node Secret for each Authentication Agent (ISA Server)
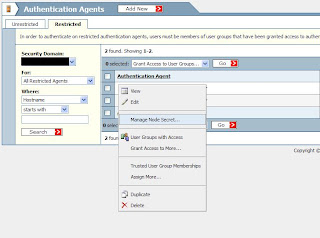
In the RSA Security Console, go to 'Access', 'Authentication Agents' and 'Manage Existing'
.
Click the arrow next tot he appropriate ISA Server and select 'Manage Node Secret...'
On the RSA AM server Locate agent_nsload.exe and copy to each ISA Server in the array
Set a node secret in RSA AM interface on each Agent entry and download .zip files when requested
Extract the NODESECRET.REC file from the supplied .zip and place with the agent_nsload.exe
To import the node secret to the ISA Server(s), run the following command
agent_nsload.exe -f <path to nodesecret.rec> -p <node secret password>
A 'securid' file should then be created in C:\Windows\System32\ (note the lack of file extension). This file should then be copied to the "C:\Program Files\Microsoft ISA Server\sdconfig\"
That was enough to get ISA working with RSA 7.1 SP2.